Use an independent intermediate certificate authority
The built-in Puppet certificate authority automatically generates a root and intermediate certificate, but if you need additional intermediate certificates or prefer to use a public authority CA, you can set up an independent intermediate certificate authority. You must complete this configuration during installation.
- Take note of the
Next Updatedates of the CRLs for your entire chain of trust. - Submit updated CRLs to Puppet Server using the Certificate Revocation List endpoint.
- Configure agents to download CRL updates by setting
crl_refresh_intervalin thepuppet_enterprise::profile::agentclass.
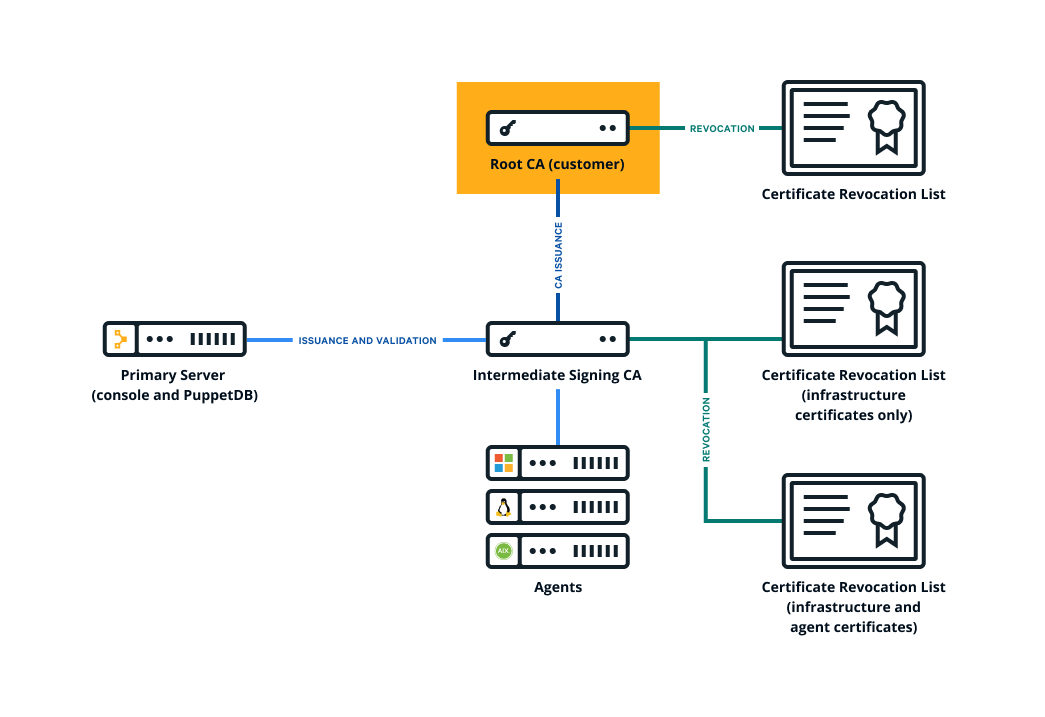
- Collect the PEM-encoded certificates and CRLs for your organization's chain of trust, including the root certificate, any intermediate certificates, and the signing certificate. (The signing certificate might be the root or intermediate certificate.)
- Create a private RSA key, with no passphrase, for the Puppet CA.
- Create a PEM-encoded Puppet CA certificate.
- Create a CSR for the Puppet CA.
- Generate the Puppet CA certificate by signing
the CSR using your external CA.
Ensure the CA constraint is set to true and the
keyIdentifieris composed of the 160-bit SHA-1 hash of the value of the bit stringsubjectPublicKeyfield. See RFC 5280 section 4.2.1.2 for details.
- Concatenate all of the certificates into a PEM-encoded certificate bundle, starting
with the Puppet CA cert and ending with your root
certificate.
-----BEGIN CERTIFICATE----- <PUPPET CA CERTIFICATE> -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- <OPTIONAL INTERMEDIATE CA CERTIFICATES> -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- <ROOT CA CERTIFICATE> -----END CERTIFICATE-----
- Concatenate all of the CRLs into a PEM-encoded CRL chain, starting with any
optional intermediate CA CRLs and ending with your root certificate CRL.
-----BEGIN X509 CRL----- <OPTIONAL INTERMEDIATE CA CRLs> -----END X509 CRL----- -----BEGIN X509 CRL----- <ROOT CA CRL> -----END X509 CRL-----
The PE installer automatically generates a Puppet CRL during installation, so you don't have to manage the Puppet CRL manually. - Copy your CA bundle (from step 4), CRL chain (from step 5), and
private key (from step 2) to the node where you're installing the primary server. Allow access to your private key only from the PE installation process, which runs as root.
- Install PE using a customized
pe.conffile withsigning_caparameters:./puppet-enterprise-installer -c <PATH_TO_pe.conf>In your customized
pe.conffile, you must include three keys for thesigning_caparameter:bundle,crl_chain, andprivate_key.{ "pe_install::signing_ca": { "bundle": "/root/ca/int_ca_bundle" "crl_chain": "/root/ca/int_crl_chain" "private_key": "/root/ca/int_key" } } - Optional: Validate that the CA is working by running
puppet agent -tand verifying your intermediate CA with OpenSSL.openssl x509 -in /etc/puppetlabs/puppet/ssl/ca/signed/<HOSTNAME>.crt -text -noout Certificate: Data: Version: 3 (0x2) Serial Number: 1 (0x1) Signature Algorithm: sha256WithRSAEncryption Issuer: CN=intermediate-ca ...
Related information






